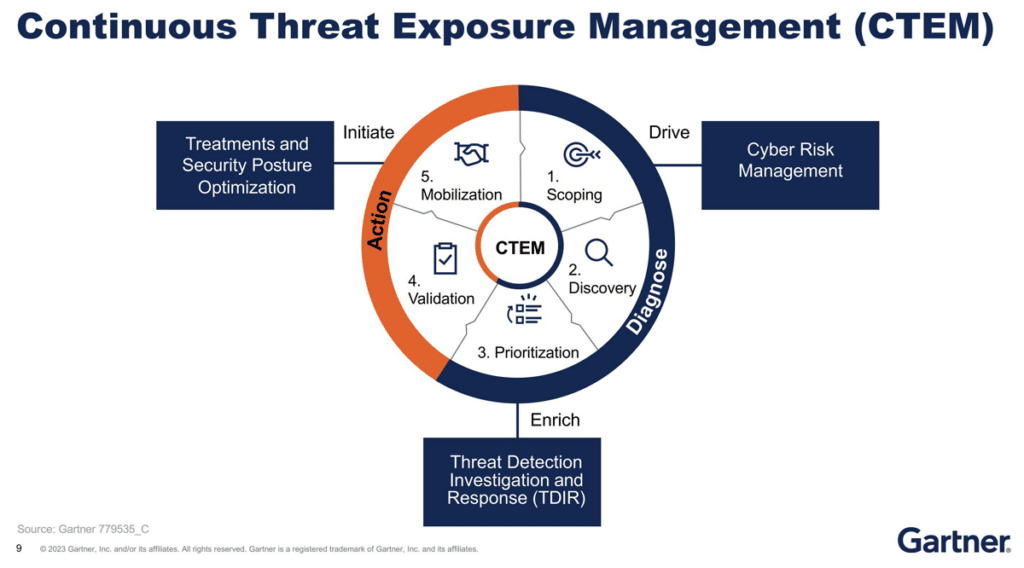
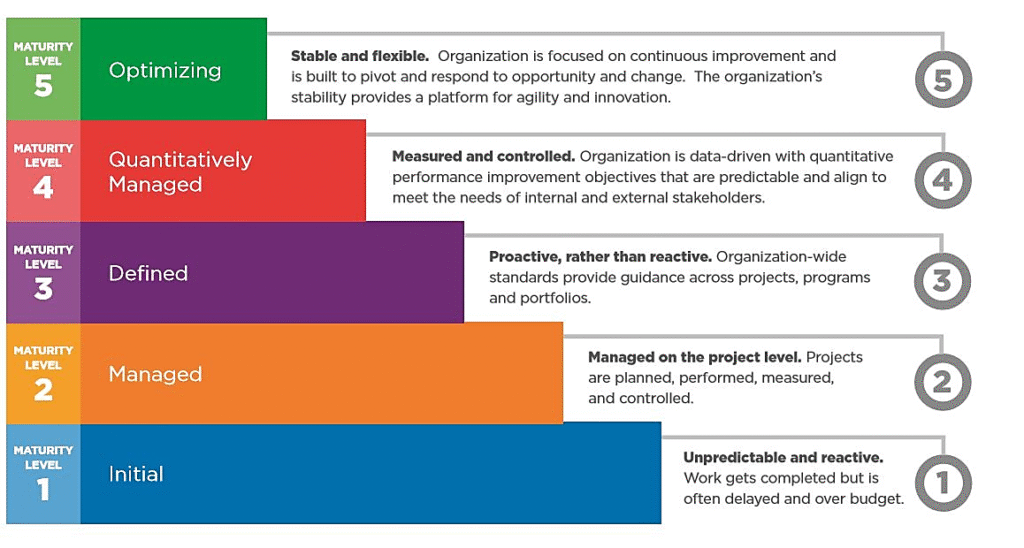
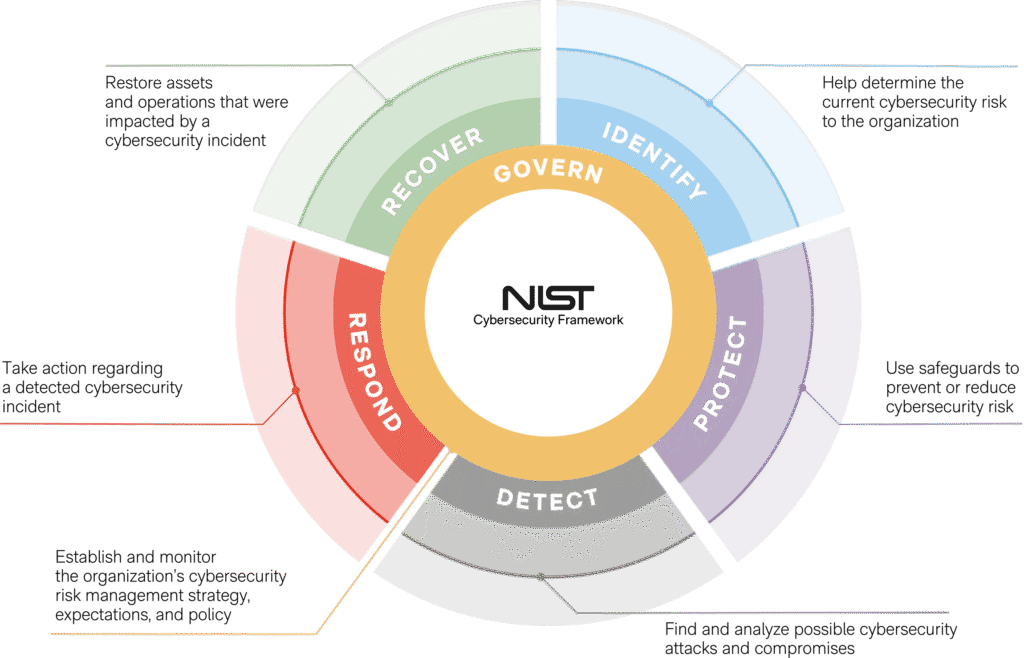
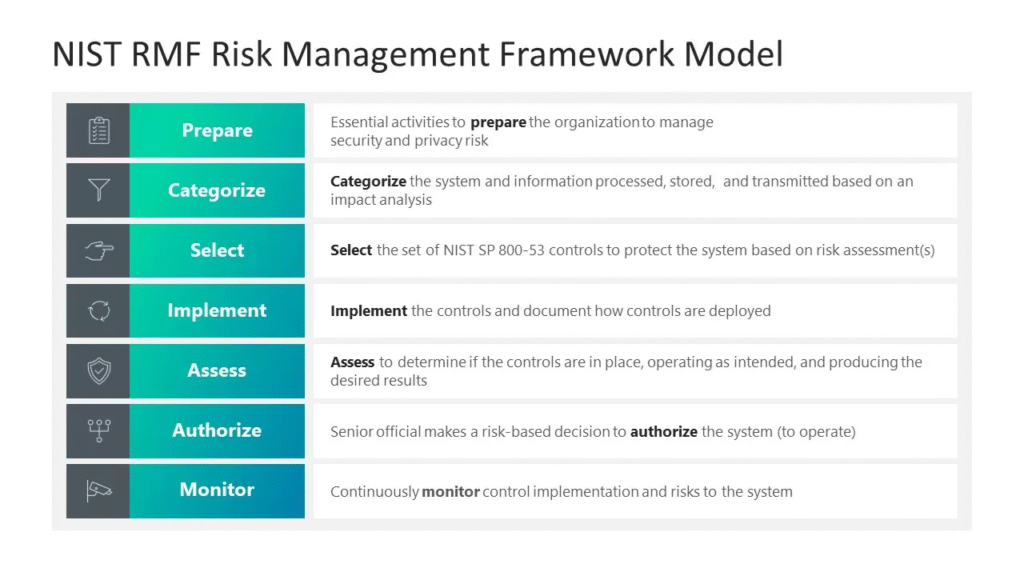
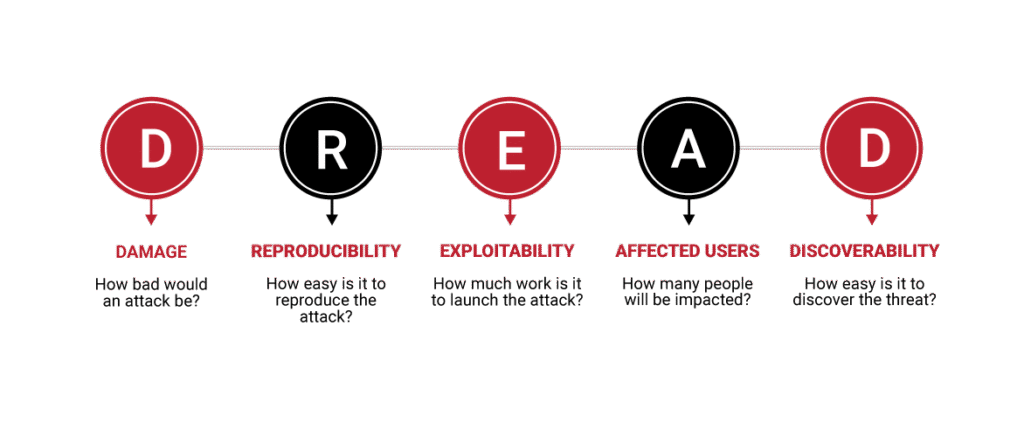
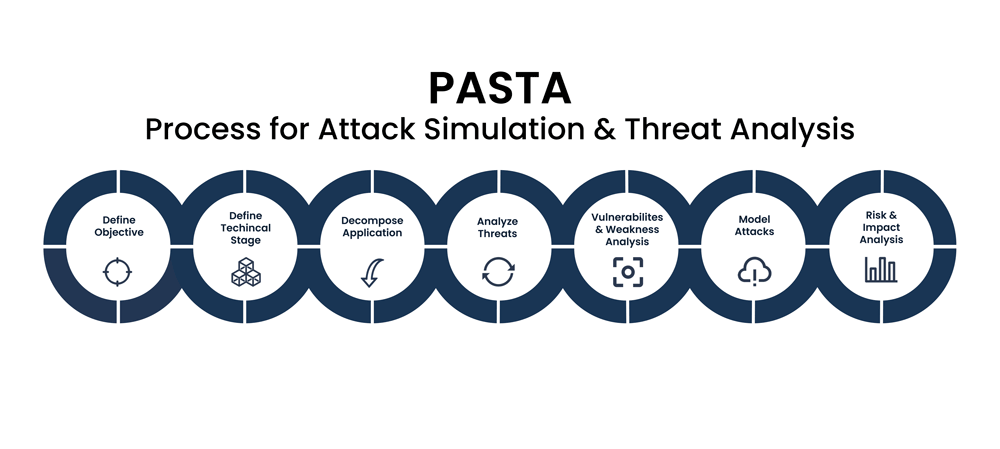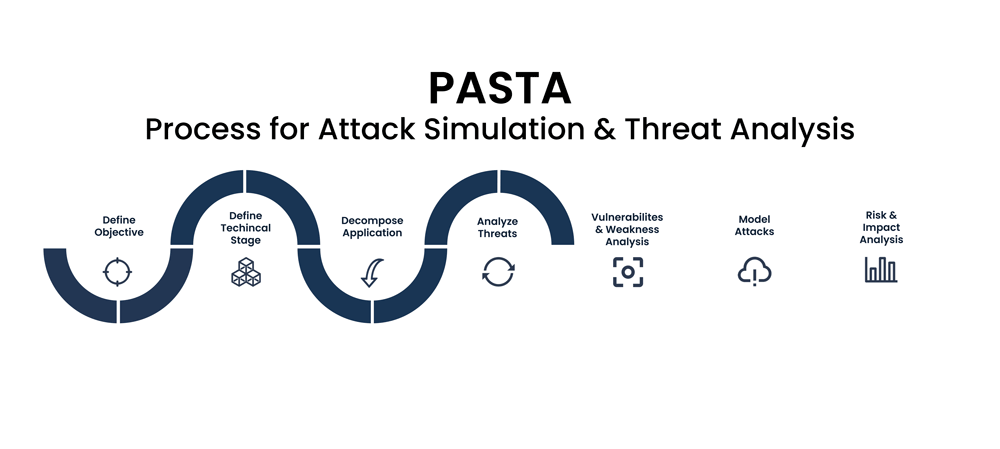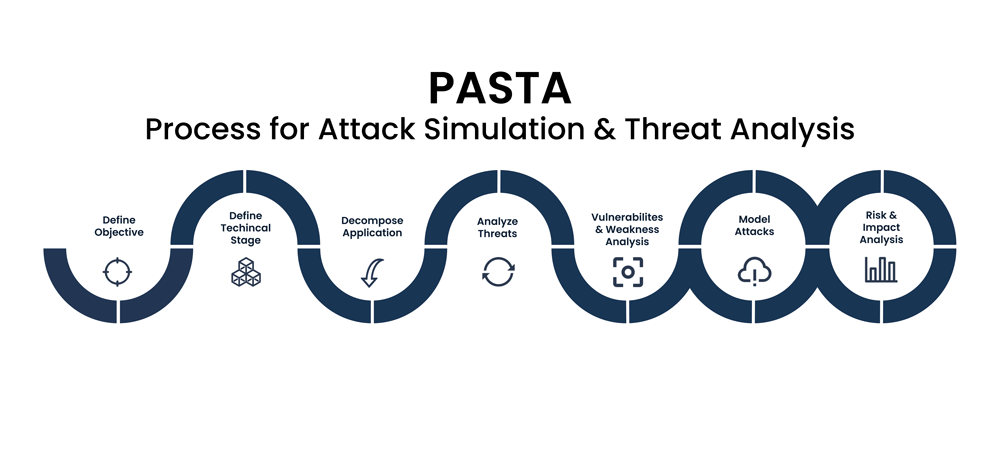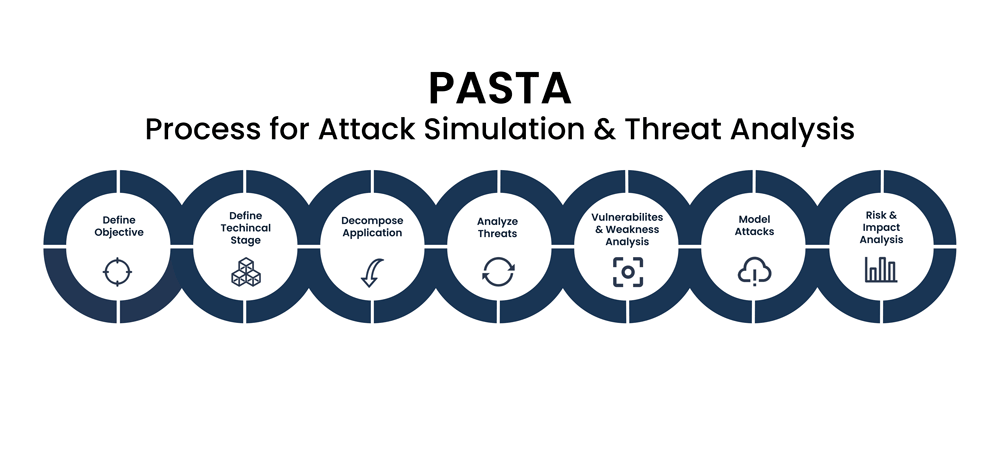
Reading Time: 2 minutesGenerating a PEM file from a Root Certificate Authority (Root CA) in Microsoft ADCS involves exporting the root certificate and converting it into the PEM format, which is commonly used in Linux environments, web servers, and various security applications. Note Read More …