
Reading Time: 3 minutesDelivery management in software development ensures software products are planned, developed, tested, and delivered efficiently, on time, and with high quality.
Meeting of Brilliant Syche – IT Pro's Corner
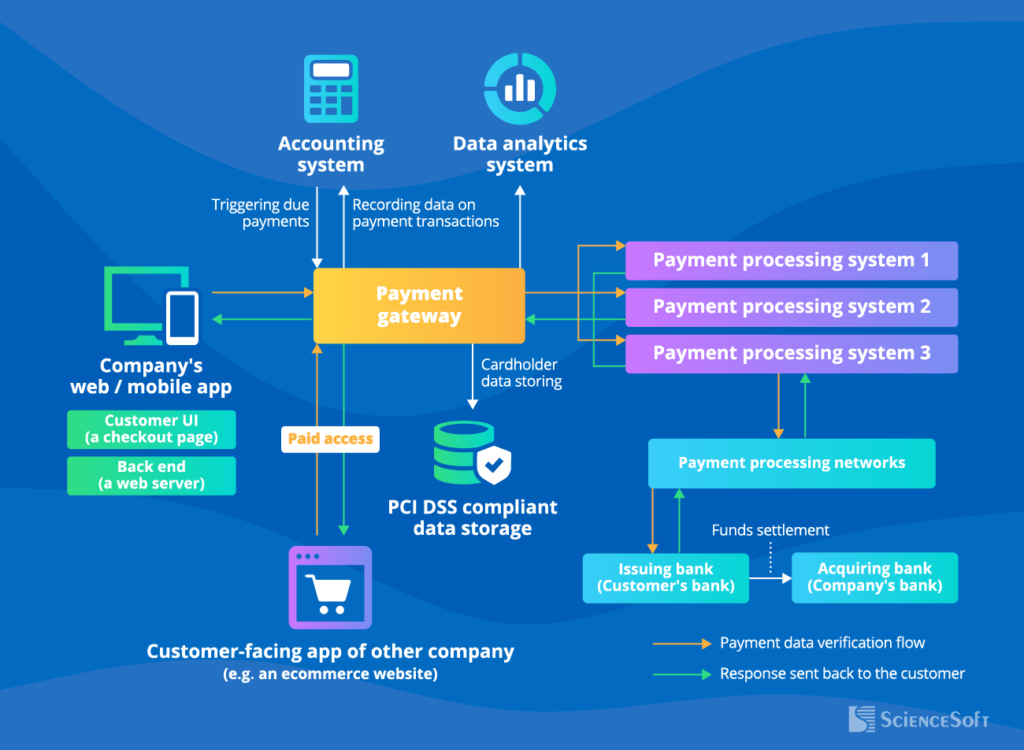
Reading Time: 2 minutesA payment gateway is a secure interface that facilitates online transactions by acting as a bridge between customers, merchants, and financial institutions. It ensures the secure transfer of payment data, processes transactions, and communicates the results back to the merchant’s system. Payment gateways are integral to e-commerce platforms, enabling seamless and secure payment experiences.

Reading Time: 3 minutesCybersecurity leadership is no longer optional—it’s a board-level priority. As digital threats escalate and compliance frameworks tighten, organizations face a critical decision: should they appoint a full-time, in-house Chief Information Security Officer (CISO) or engage a Virtual CISO (vCISO) for flexible, outsourced expertise?
Reading Time: 2 minutesISO 8583 is an international standard for financial transaction card originated interchange messaging. It defines a message format and a communication flow so that different systems can exchange transaction requests and responses. This standard is widely used in electronic transactions Read More …

Reading Time: 7 minutesHere’s a comprehensive “Code Review” checklist that integrates controls from OWASP, ISO 27001, NIST SSDF, PCI DSS, CIS Controls, and GRC frameworks. It’s structured in a way so you can directly export it into Excel — each row represents a Read More …

Reading Time: 2 minutesBest Practices for SSD Protection Step-by-Step Windows 11 Configuration 1. Check TRIM Status 2. Disable Hibernation (Optional) 3. Adjust Virtual Memory (Paging File) 4. Enable Write Caching 5. Keep SSD Firmware Updated 6. Maintain Free Space 7. Avoid Defragmentation Extra Read More …
Reading Time: 3 minutesGovernance, Risk, and Compliance (GRC) is an integrated organizational strategy designed to manage corporate governance, identify and mitigate risks, and ensure ongoing compliance with industry standards and government regulations. It also refers to specialized software suites that help implement and Read More …

Reading Time: 2 minutesGenerating a PEM file from a Root Certificate Authority (Root CA) in Microsoft ADCS involves exporting the root certificate and converting it into the PEM format, which is commonly used in Linux environments, web servers, and various security applications. Note Read More …

Reading Time: 5 minutesUnderstand the significance of the COSO framework in your organization’s internal control strategy for improved governance, risk management, and compliance measures. In today’s complex business environment, organizations face a multitude of risks ranging from financial misstatement and operational inefficiencies to Read More …

Reading Time: 4 minutesStatus: Final Blueprint (Summary) Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: September 14, 2025 Location: Dhaka, Bangladesh Version: 1.0 1. The Strategic Imperative: The 10-Minute Cloud Breach The fundamental nature of cybersecurity has shifted. Read More …

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: September 12, 2025 Location: Dhaka, Bangladesh Version: 1.0 The paradigm for securing enterprise cloud environments is undergoing a fundamental transformation. Traditional, siloed security tools Read More …

Reading Time: 3 minutesDetection‑as‑Code (DaC) is moving from niche practice to mainstream SOC engineering discipline. By embedding detection logic into CI/CD‑style pipelines, organizations are achieving faster deployment cycles, higher detection accuracy, and measurable reductions in false positives.
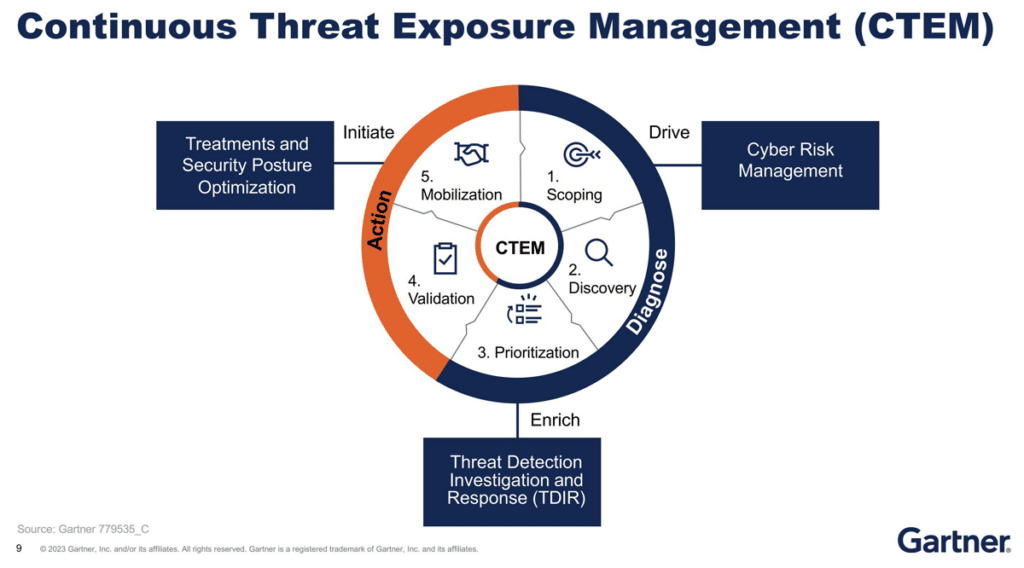
Reading Time: 3 minutesFor years, security teams have relied on separate tools to manage cloud misconfigurations (CSPM), Kubernetes security (KSPM), and sensitive data exposure (DSPM). Meanwhile, Continuous Threat Exposure Management (CTEM) emerged as a programmatic approach to continuously identify, assess, and remediate exposures across the attack surface.

Reading Time: 2 minutesAI-driven tools can craft highly targeted, multilingual phishing emails by scraping OSINT, leaked credentials, and social media profiles. Deepfake voice generators mimic executives’ tone and emotional cues, making human detection far more difficult. Services like PhishGPT+ enable automated spear-phishing campaigns tailored by geolocation, language, and psychological triggers.

Reading Time: 5 minutesModern Security Operations Centers (SOCs) face an escalating challenge: an overwhelming volume of security alerts, coupled with persistent manual inefficiencies and a severe global talent shortage. This leads to alert fatigue, a reactive posture, and a heightened risk of missing critical incidents. The traditional manual approach to incident response is no longer sustainable against the speed and sophistication of contemporary cyber threats.

Reading Time: 5 minutesStatus: Final BlueprintAuthor: Shahab Al Yamin ChawdhuryOrganization: Principal Architect & Consultant GroupResearch Date: April 2, 2025Location: Dhaka, BangladeshVersion: 1.0 1. Executive Summary and Strategic Imperatives The “SOAR Playbook for Malware Containment” outlines Security Orchestration, Automation, and Response (SOAR) as a Read More …

Reading Time: 4 minutesThe escalating threat of phishing demands a transformative approach to cybersecurity. This “SOAR Playbook for Phishing Email Investigation” leverages Security Orchestration, Automation, and Response (SOAR) to convert reactive security operations into a proactive, efficient, and scalable defense. By automating repetitive tasks and orchestrating complex workflows, SOAR drastically reduces Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) for phishing incidents, often to mere minutes.

Reading Time: 5 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: April 9, 2025 Location: Dhaka, Bangladesh Version: 1.0 I. Executive Summary The modern cybersecurity landscape is challenged by an overwhelming volume of security alerts Read More …

Reading Time: 6 minutesThis blueprint outlines the integration of Security Orchestration, Automation, and Response (SOAR) with proactive Threat Hunting. This synergy shifts organizations from reactive to proactive defense, enhancing cybersecurity posture, improving Security Operations Center (SOC) efficiency, and accelerating response times to advanced threats. Key recommendations include phased implementation, KPI-driven measurement, continuous improvement, and investment in human capital.

Reading Time: 3 minutesThis blueprint outlines a transformative approach to vulnerability management (VM) by integrating Security Orchestration, Automation, and Response (SOAR) platforms. Traditional manual VM processes are overwhelmed by cyber threats. SOAR shifts VM from reactive, labor-intensive tasks to a proactive, automated, and integrated security function, enhancing speed, accuracy, and operational effectiveness.

Reading Time: 8 minutesThis blueprint outlines a comprehensive Security Orchestration, Automation, and Response (SOAR) playbook to combat cryptojacking—the unauthorized use of computing resources for cryptocurrency mining. Cryptojacking poses significant financial, operational, and reputational risks by silently consuming CPU cycles, increasing power costs, degrading system performance, and introducing hidden vulnerabilities.

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: March 15, 2025 Location: Dhaka, Bangladesh Version: 1.0 Table of Contents 1. Executive Summary This “SOAR Playbook for Ransomware” offers a comprehensive blueprint for Read More …

Reading Time: 5 minutesThe escalating volume and sophistication of cyber threats, coupled with a shortage of security professionals, necessitate a shift from manual incident response (IR) to automated solutions. Security Orchestration, Automation, and Response (SOAR) platforms offer a transformative approach by consolidating security operations, automating repetitive tasks, and streamlining incident handling.

Reading Time: 5 minutesThis blueprint provides a comprehensive framework for preparing for, responding to, and recovering from ransomware attacks. It emphasizes cyber resilience as a strategic imperative, integrating proactive defense, swift incident response, and continuous improvement to minimize impact and ensure business continuity.

Reading Time: 3 minutesThis blueprint outlines a comprehensive strategy to transform an organization’s communications and collaboration infrastructure, fostering agility, productivity, and competitive advantage. It emphasizes a phased, user-centric, security-by-design approach, aiming for improved operational efficiency, enhanced employee experience, and measurable ROI.

Reading Time: 6 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: March 29, 2025 Location: Dhaka, Bangladesh Version: 1.0 1. Executive Summary Ransomware has evolved into a sophisticated, multi-stage cyber threat causing significant financial, operational, Read More …

Reading Time: 5 minutesBlueprint Details 1. Executive Summary: The Imperative for Smarter Threat Prioritization The cybersecurity landscape is overwhelmed by an ever-increasing volume of vulnerabilities, with over 25,000 new CVEs reported in 2022 alone. Traditional vulnerability management, often relying solely on CVSS scores, Read More …

Reading Time: 6 minutesData Loss Prevention (DLP) is a crucial cybersecurity strategy designed to detect and prevent data breaches by blocking unauthorized extraction or exposure of sensitive data. It combines people, processes, and technology to identify, classify, and apply usage policies to sensitive information across endpoints, networks, and cloud platforms (data at rest, in motion, and in use).

Reading Time: 6 minutesExtended Detection and Response (XDR) is a pivotal evolution in enterprise cybersecurity. It unifies, intelligently, and automates threat detection, investigation, and response by aggregating telemetry from endpoints, networks, cloud, identity, and email into a single platform. This holistic visibility, powered by AI/ML, detects complex attacks, reduces alert fatigue, and accelerates incident containment.

Reading Time: 7 minutesCybersecurity assessment frameworks are structured methodologies guiding organizations to establish and maintain robust cybersecurity postures. They provide a roadmap for identifying, assessing, and managing risks to digital assets, enhancing resilience, streamlining operations, and building trust. Cybersecurity is a core business enabler, requiring agile, adaptive security, strong governance, and leveraging a complementary ecosystem of frameworks to tailor security to unique needs.
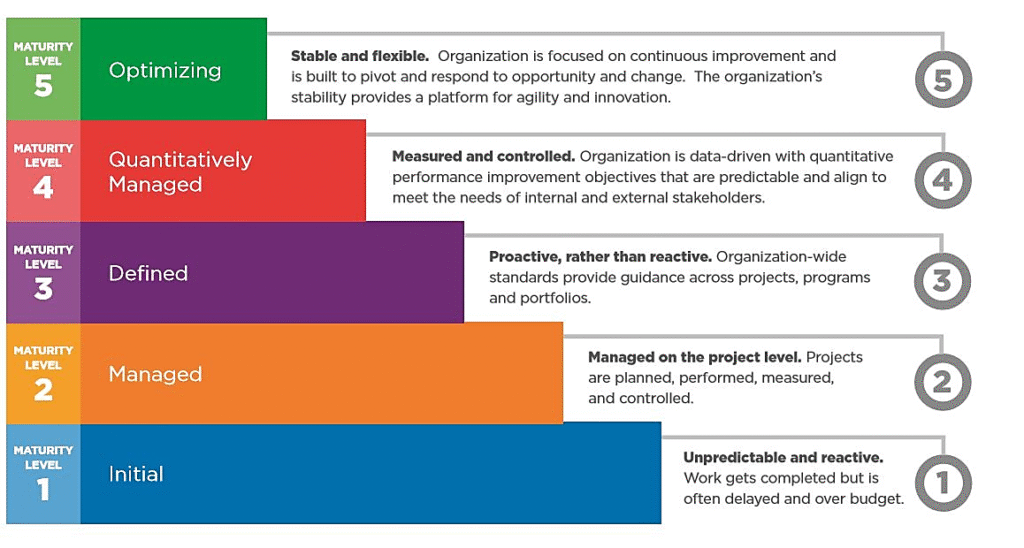
Reading Time: 4 minutesThis document provides a concise overview of the “Implementation Plan – SOC-CMM” research blueprint, synthesizing key insights for establishing, maturing, and optimizing Security Operations Center (SOC) capabilities. It highlights the core framework, implementation lifecycle, and critical areas for optimization across people, processes, technology, performance, and compliance.
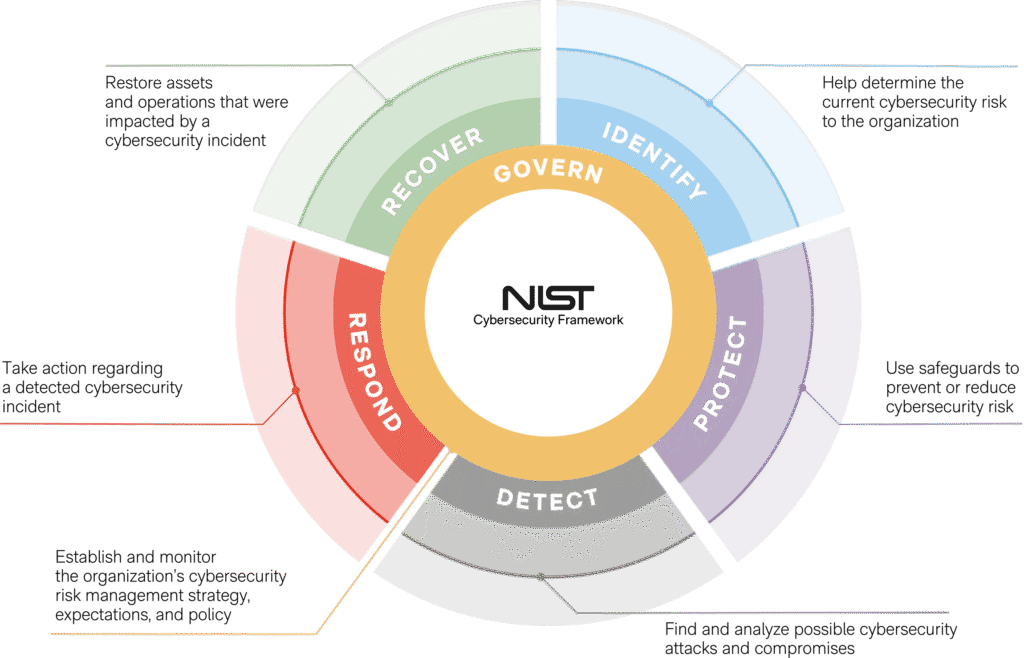
Reading Time: 5 minutesThis blueprint outlines a strategic and actionable plan for implementing the NIST Cybersecurity Framework (CSF) 2.0, the leading global standard for managing cyber risk. It emphasizes a proactive, governance-driven approach to enhance organizational resilience, optimize resource allocation, and streamline compliance, transforming cybersecurity into a core business enabler.

Reading Time: 6 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: March 17, 2025 Location: Dhaka, Bangladesh Version: 1.0 Executive Summary The “Implementation Plan – NIST AI RMF” provides a comprehensive roadmap for large enterprises Read More …

Reading Time: 4 minutesThis document outlines a blueprint for deploying a robust Single Sign-On (SSO) solution centered on Active Directory. The initiative’s primary goal is to enhance enterprise security, streamline IT operations, and significantly improve the end-user experience by unifying application access.

Reading Time: 3 minutesn today’s complex digital landscape, securing your organization requires moving beyond simple checklists. You need a strategy that focuses on what truly matters: your most critical business assets. This is where the Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE) framework comes in. Developed by Carnegie Mellon University’s Software Engineering Institute (SEI), OCTAVE provides a risk-based approach to threat modeling that aligns security efforts with business goals.
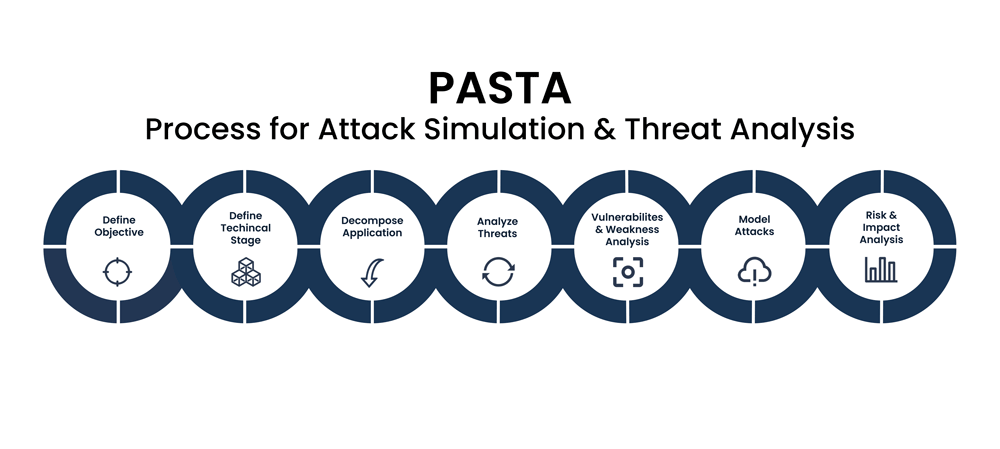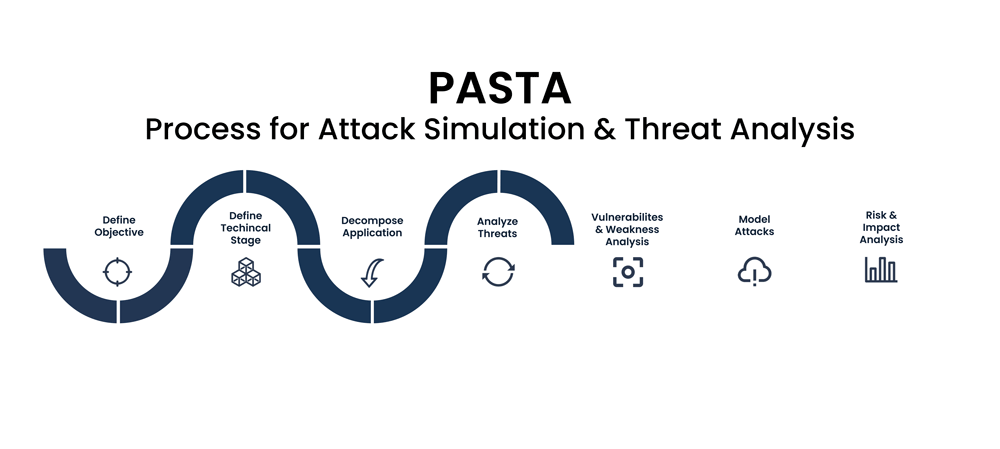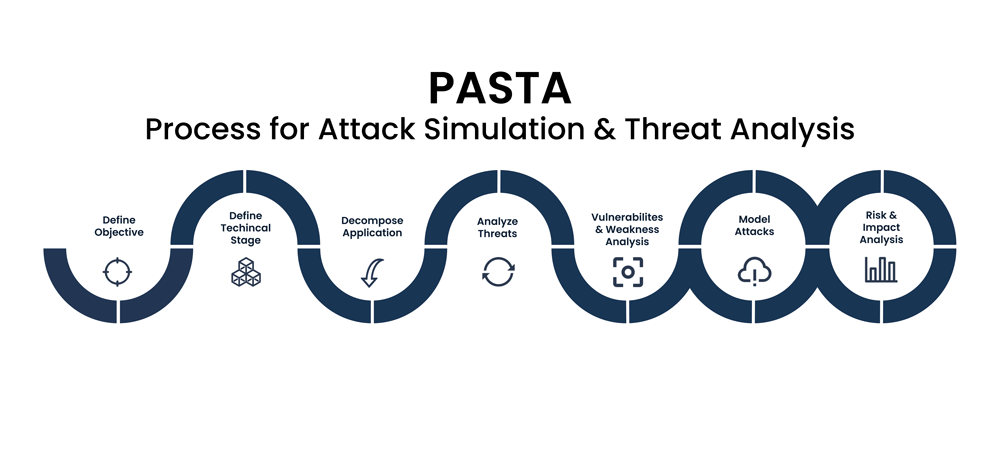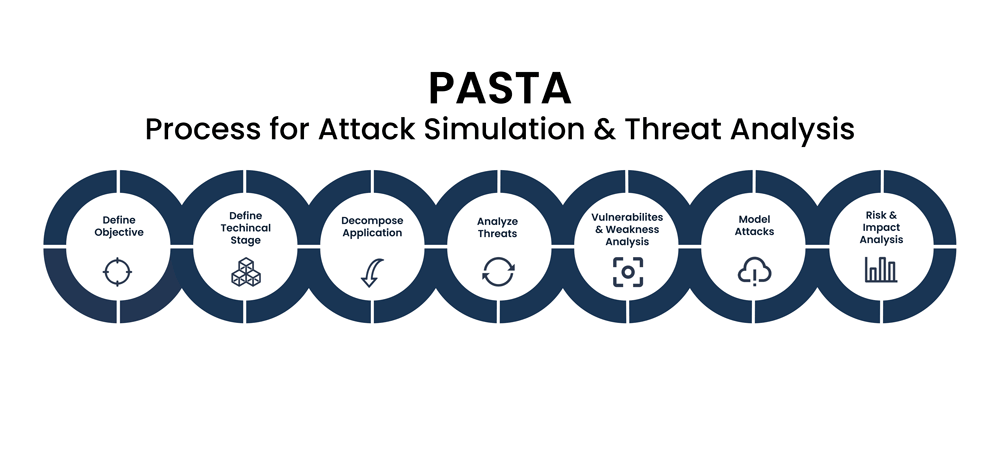
Reading Time: 4 minutesThis document outlines the PASTA-SOC framework, a structured methodology to evolve a Security Operations Center (SOC) from a reactive to a proactive, threat-informed defense model. It operationalizes the seven stages of the Process for Attack Simulation and Threat Analysis (PASTA) by integrating its business-centric principles with the tactical capabilities of modern security technologies, primarily Breach and Attack Simulation (BAS), Threat Intelligence Platforms (TIPs), and Security Orchestration, Automation, and Response (SOAR).

Reading Time: 4 minutesStatus: Final Blueprint Author: Shahab Al Yamin Chawdhury Organization: Principal Architect & Consultant Group Research Date: March 1, 2025 Location: Dhaka, Bangladesh Version: 1.0 Part I: Strategic Foundations and Governance This section establishes the strategic “why” for the SIEM & Read More …