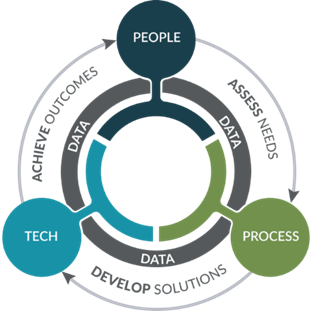
Let’s break down the importance of people, process, technology, and data in a Cybersecurity Operations Center (SOC): People: The SOC is staffed by a team of skilled security professionals, including security analysts, incident responders, threat intelligence analysts, and security engineers. Read More …