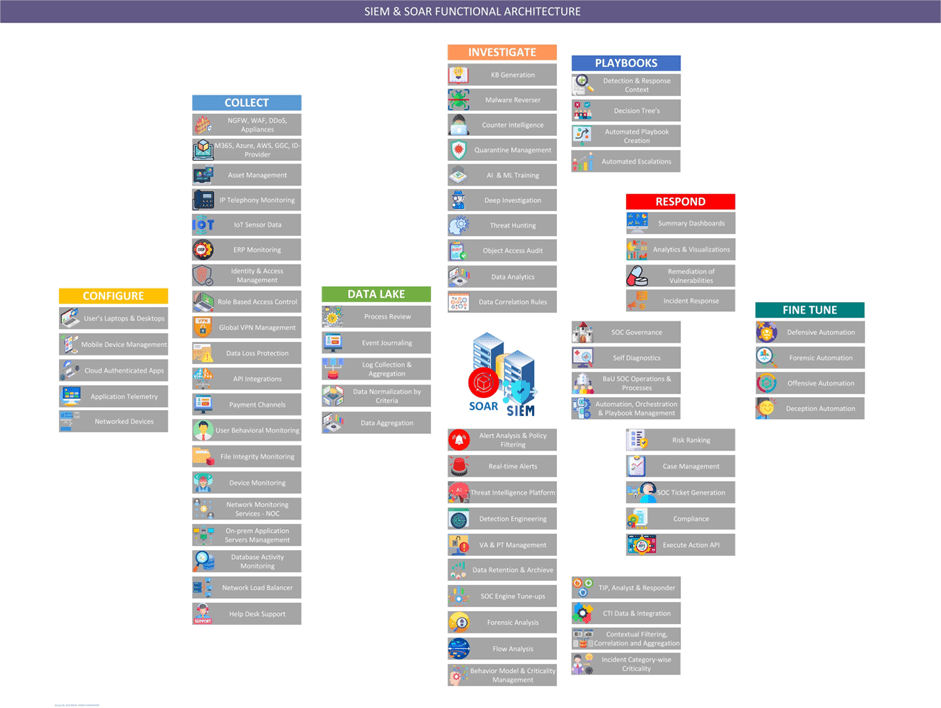
In today’s rapidly evolving digital landscape, organizations face an ever-increasing threat of cyberattacks. To fortify their defenses, they must adopt a comprehensive approach that combines industry standards, advanced detection mechanisms, and proactive strategies. In this blog post, we explore the Read More …