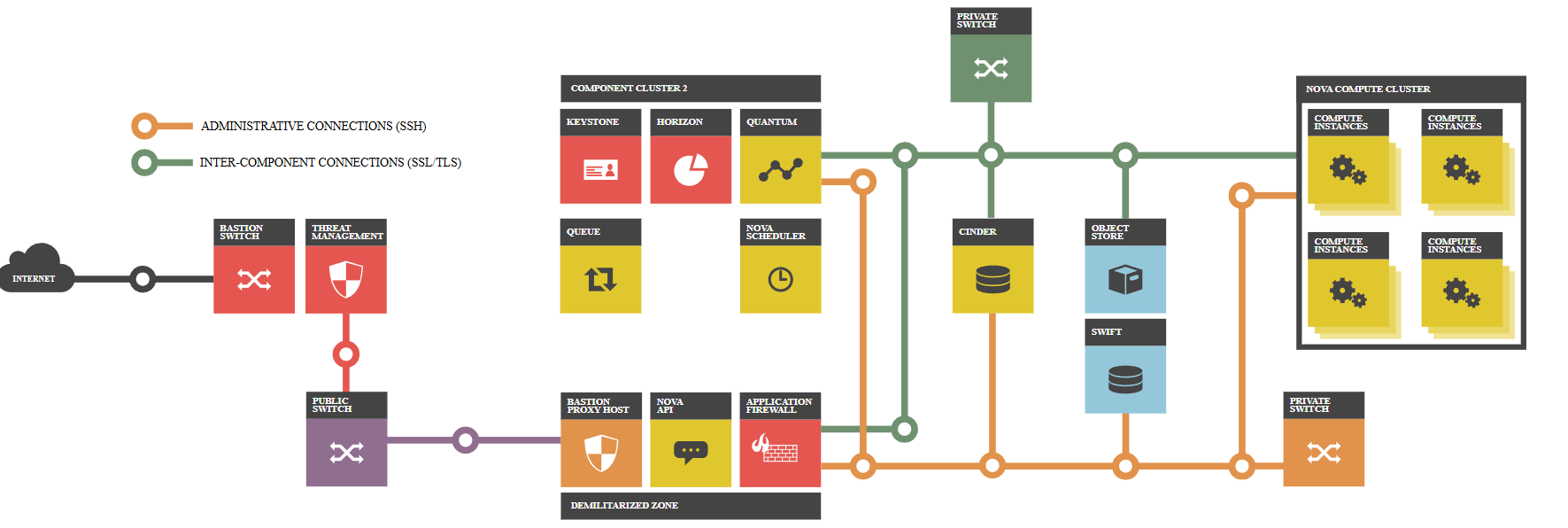
Have you ever encountered the following questions asked by your superiors or you peers?
How to manage cloud security posture management for OpenStack?
- What are the key parts to look out for?
- What are the best practices?
- How to implement CSPM?
- And how to manage privacy?
There are hefty of items that you can think of, but lets focus on the top high level items, and elaborate briefly:
Managing cloud security posture management (CSPM) for OpenStack involves several key steps and best practices to ensure a robust and secure cloud environment. Here’s a comprehensive guide:
Key Parts to Look Out For
- Continuous Monitoring and Compliance: Ensure continuous monitoring of your cloud environment to detect misconfigurations, unauthorized access, and compliance violations.
- Automated Policy Enforcement and Remediation: Implement automated tools to enforce security policies and remediate issues promptly.
- Centralized Dashboard and Reporting: Use a centralized dashboard to manage and report on security and compliance across your cloud infrastructure.
- Threat Intelligence and Vulnerability Management: Integrate threat intelligence to identify and manage vulnerabilities effectively.
- Scalability and Performance: Ensure the CSPM solution can scale with your cloud environment and maintain performance.
- User-Friendly Interface and Ease of Use: Choose a CSPM tool that is easy to use and understand.
Best Practices
- Protect Against Common Misconfigurations: Establish robust configuration management protocols to monitor and document changes to your cloud-based assets.
- Define Security Policies and Standards: Create comprehensive security policies and standards that cover access controls, data encryption, network segmentation, and compliance requirements.
- Implement Automation and Orchestration: Use automation tools to enforce security policies and orchestrate remediation processes.
- Protect Against Internal Breaches: Implement measures to protect against internal threats and ensure proper access controls.
- Remediate Found Issues Quickly: Address security issues and vulnerabilities as soon as they are detected.
- Discover and Inventory Assets: Maintain an up-to-date inventory of all cloud assets and configurations.
- Choose the Right CSPM Tool: Select a CSPM tool that fits your specific needs and integrates well with your cloud environment.
- Discover Misuse and Compliance Violations: Continuously monitor for misuse and compliance violations.
Implementing CSPM
- Assess Your Current Security Posture: Conduct a thorough assessment of your current cloud security posture to identify gaps and vulnerabilities.
- Select a CSPM Tool: Choose a CSPM tool that meets your requirements and integrates with your OpenStack environment.
- Configure and Deploy the Tool: Set up the CSPM tool and configure it to monitor your cloud environment continuously.
- Monitor and Analyze: Use the CSPM tool to monitor your cloud environment and analyze the data for potential security issues.
- Remediate Issues: Address any identified issues promptly to maintain a strong security posture.
- Review and Improve: Regularly review the effectiveness of your CSPM implementation and make improvements as needed.
Managing Privacy
- Data Encryption: Encrypt sensitive data both in transit and at rest to protect it from unauthorized access.
- Access Controls: Implement strict access controls to ensure that only authorized personnel can access sensitive data.
- Data Minimization: Collect and store only the minimum amount of data necessary for your operations to reduce the risk of data breaches.
- Regular Audits: Conduct regular audits of your data handling practices to ensure compliance with privacy regulations.
- Incident Response Plan: Develop and maintain an incident response plan to address any data breaches or privacy incidents promptly.
By following these steps and best practices, you can effectively manage your cloud security posture and ensure the privacy of your data in an OpenStack environment.