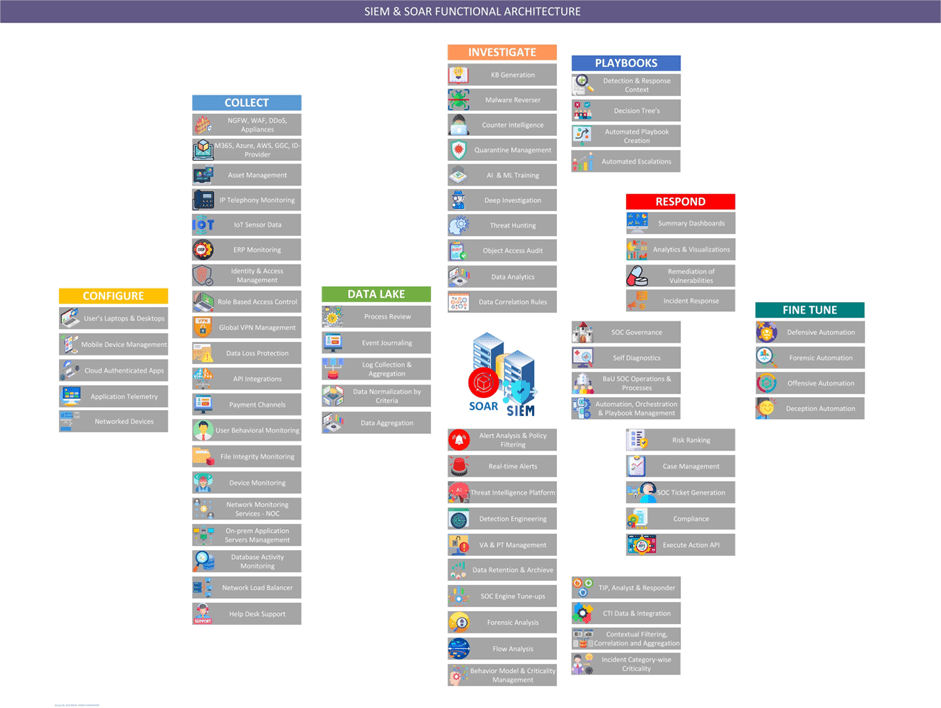
In the world of cybersecurity, integration between different tools and platforms is crucial for effective threat detection and response. In this blog post, we will guide you on integrating Wazuh, an open-source Security Information Event Management (SIEM) and XDR solution, with Read More …