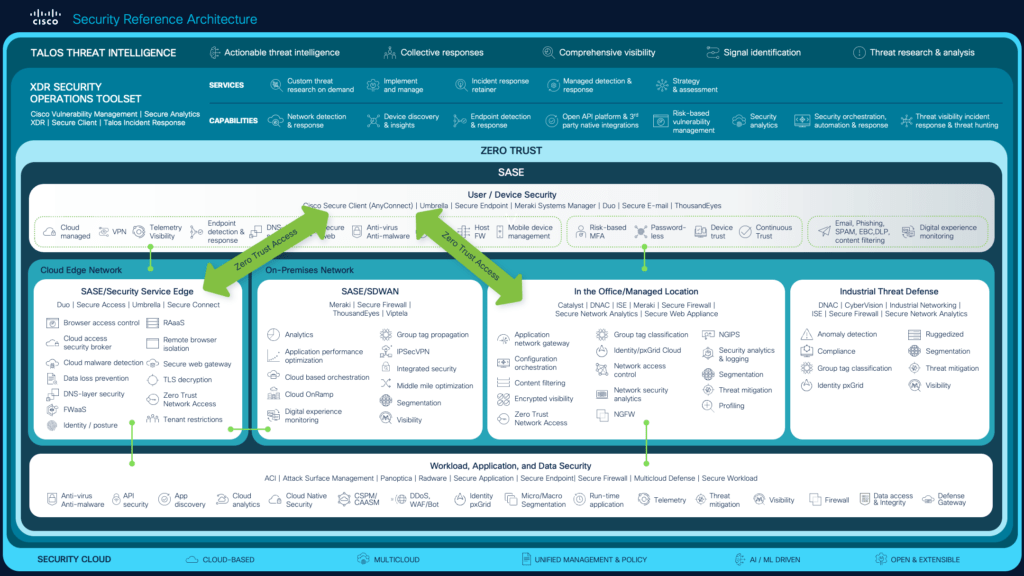
Here are some common Security Operations Center (SOC) technologies that play a crucial role in detecting, analyzing, and responding to security threats: A CSOC Manages all the above networked devices insights, data collected from log shipping Remember, a well-integrated combination of these Read More …
