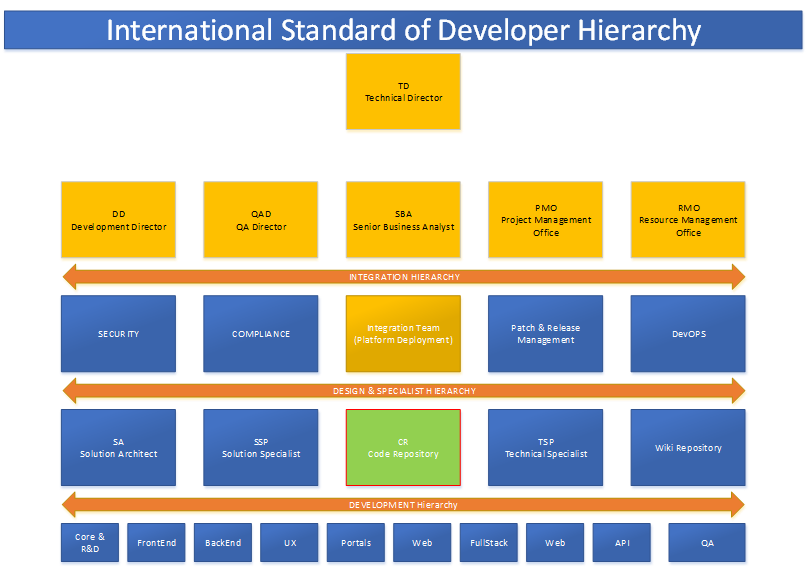
Development Hierarchy Framework Introduction to Secure Development Lifecycle (SDLC) – Discover how integrating security practices into every phase of the software development process can mitigate security risks and protect sensitive data. Learn more in our latest blog post! Benefits of Read More …