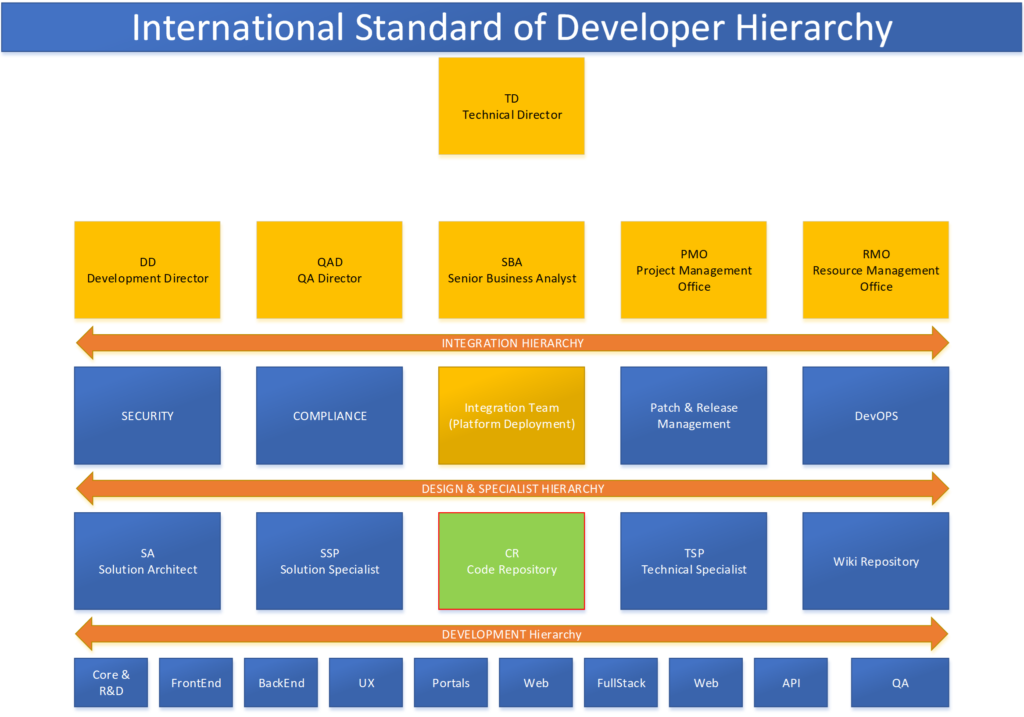
Development Hierarchy Framework
Introduction to Secure Development Lifecycle (SDLC) – Discover how integrating security practices into every phase of the software development process can mitigate security risks and protect sensitive data. Learn more in our latest blog post! Benefits of SDLC Implementation Early detection of security vulnerabilities Reduced cost of fixing security issues
Enhanced customer trust and loyalty Compliance with regulatory requirements
Key Components of SDLC
Explore the essential components of Secure Development Lifecycle (SDLC), including threat modeling, code analysis, security testing, and security training.
Best Practices for SDLC Implementation
Discover best practices for implementing SDLC, such as establishing clear security requirements, conducting regular security assessments, and integrating security testing into the development process.
An organization should enable international standards to adhere to provide a secure environment to develop in-house application platform as close to the framework as possible.
Number Of Privileged User IDs in Application Repository
The number of privileged user IDs must be strictly limited to those individuals who absolutely must have such privileges for authorized business purposes. Privileged user’s list:
| SL | Username | Employee ID | Role | Designation |
| 1 | Executive Sponsor | MD & CEO | ||
| 2 | Function Owner | CTO | ||
| 3 | Function Owner | Sr. Manager, NOC | ||
| 4 | Function Owner | Sr. Executive Manager, SOC | ||
| 5 | Function Owner | Sr. System Architect | ||
| 6 | Function Owner | QA Manager | ||
| 7 | Function Owner | IT Admin | ||
| 8 | Function Owner | Sr. DevOPS Engineer |
EXCLUSIONS OR SPECIAL CIRCUMSTANCES:
Exceptions to this policy and associated standards shall be allowed by Technical Review/Steering Committee and such approval documented and verified by the Chief Information Officer.
SYSTEMS DEVELOPMENT LIFE CYCLE (SDLC) Steps:
The minimum required phases and the tasks and considerations within these Systems development phases are outlined below.
All of the following sub-tasks and considerations, as listed in the below respective standard development phases, are mandatory if the system or software development deals with Level 1 data in any way. Otherwise, the sub-tasks and considerations are recommended steps within the required standard development phases.
System Initiation:
- A need or opportunity is defined.
- Concept proposal is made.
- An initial feasibility study is conducted.
- A project charter (if necessary) is formulated by the PMO.
- A CI/CD Pipeline is developed and output is assured by the developers.
System Requirements Analysis:
- Analyze user needs and develop user requirements.
- Create a detailed Functional Requirements Document accompanied by capacity management, where new hardware is required to provision for new micro-module placement in the Application Platform. Technical steering committee must agree on the future development and software integration requirements for hardware provisioning, and must make smooth adherence for all future software & hardware provisioning.
- Break down the system, process, or problem into discrete units or modules and utilize diagrams and other visual tools in order to analyze the situation or need.
- Any security requirements must be defined.
System Design
- This phase transforms the requirements into a Design Document.
- The functions and operations of the system or software being designed are described in detail.
- A risk analysis should be done between the System Requirements and System Design phases.
- A final design review should be done to ensure the design addresses practicality, efficiency, cost, flexibility, and security.
System Construction (Procurement):
- This phase entails the transformation of the detailed design documents into a finished product or solution.
- Manual and automated testing at a unit or module level is done throughout this phase by the system or software developers. Security considerations are taken into account during testing.
- A third-party product may be utilized as a system or software solution if it best fits the user requirements and is more practical from a budgetary and/or resource perspective. However, all of the next phases should be followed regardless of whether the solution was developed in-house or purchased.
System Testing and Acceptance:
- This phase should validate or confirm that the developed system or software meets all functional requirements as captured during the System Requirements Analysis phase.
- Representatives separate from the development group should conduct internal Quality Assurance (QA) testing.
- Representative(s) from the user group should conduct user acceptance testing.
- Documentation during testing should detail and match testing criteria to specific requirements.
- While unit and module testing should be done throughout the entire SDLC, this phase entails holistic testing of the finished product and the final acceptance testing by the user(s).
- Final security assessment testing is now conducted.
- Any problems identified during the previous phases must be resolved or remediated before implementation.