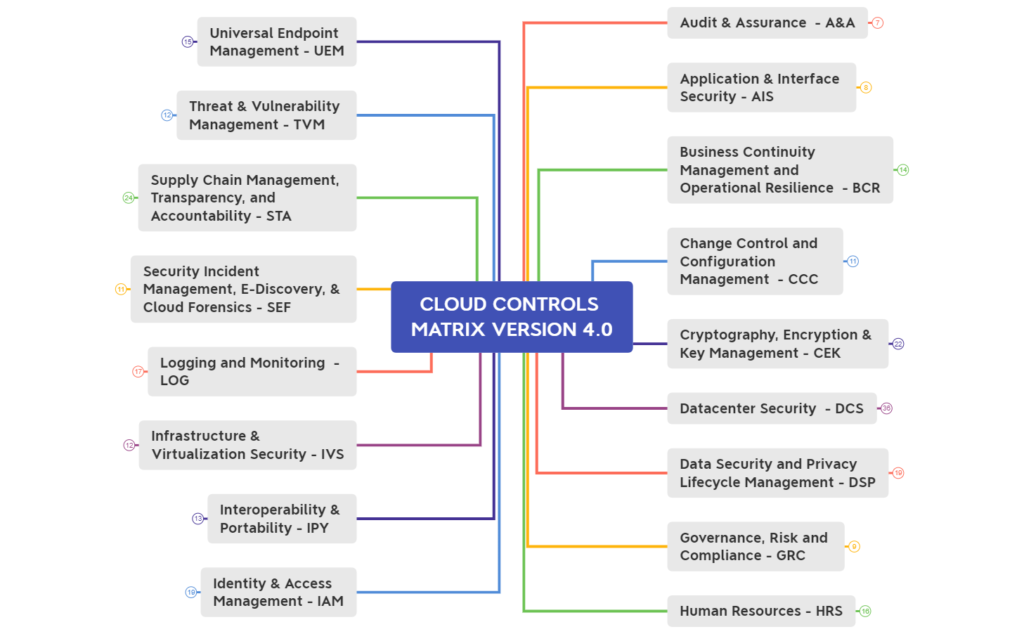
One of the most effective ways to ensure robust security in the cloud is by implementing a Cloud Security Controls Framework. What is a Cloud Security Controls Framework? A Cloud Security Controls Framework is a structured set of guidelines that Read More …