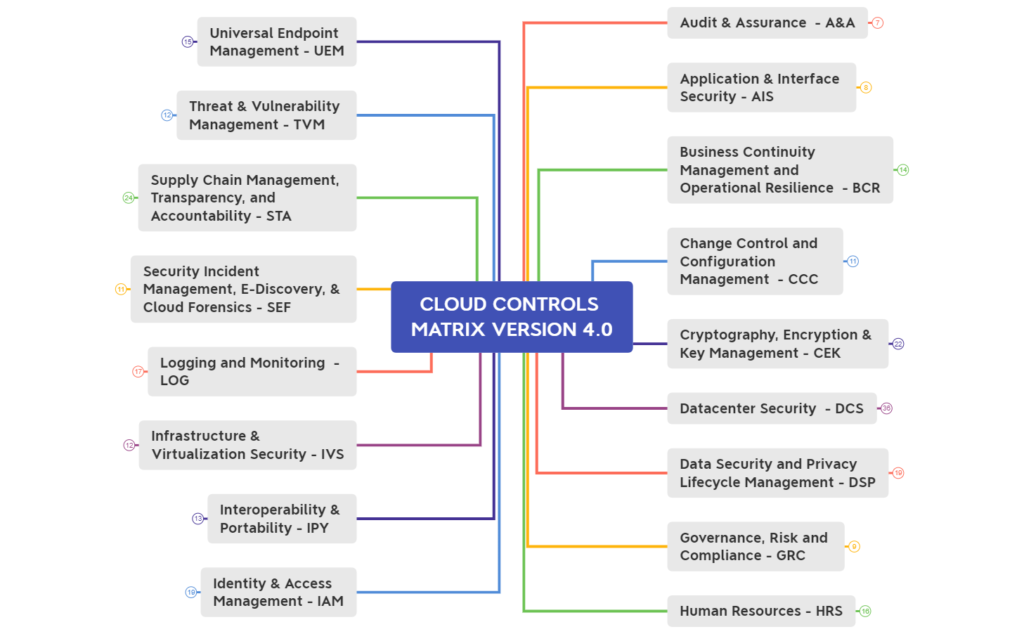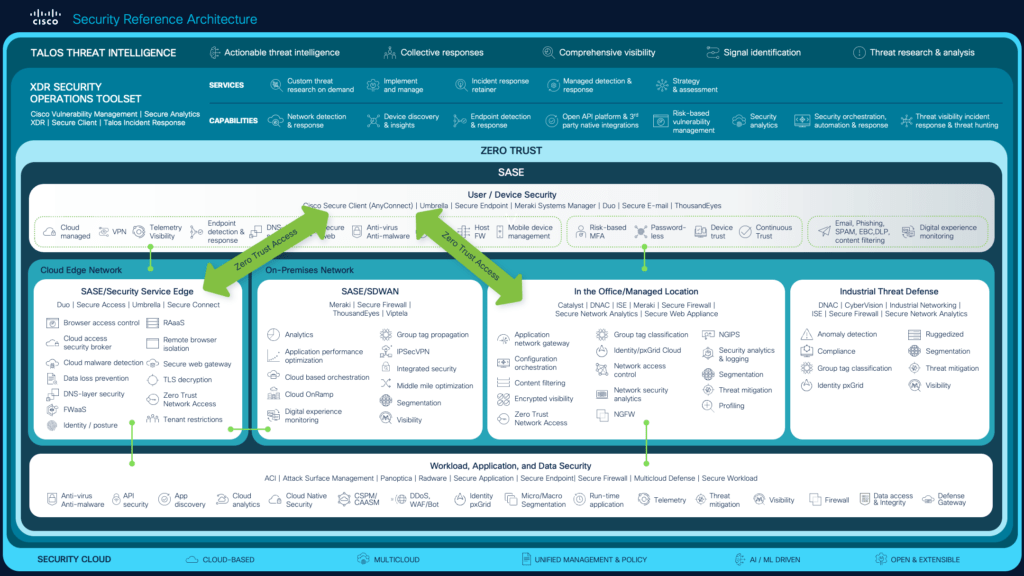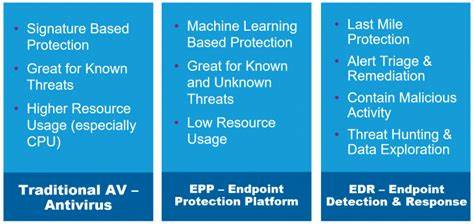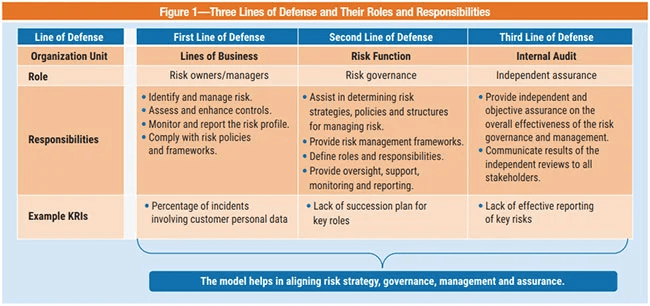
Here’s a summary of the key points from the article on integrating KRIs and KPIs for effective technology risk management: Performance Evaluation: It’s crucial for good governance and involves activities like monitoring, measurement, analysis, evaluation, internal audit, and management review. Read More …