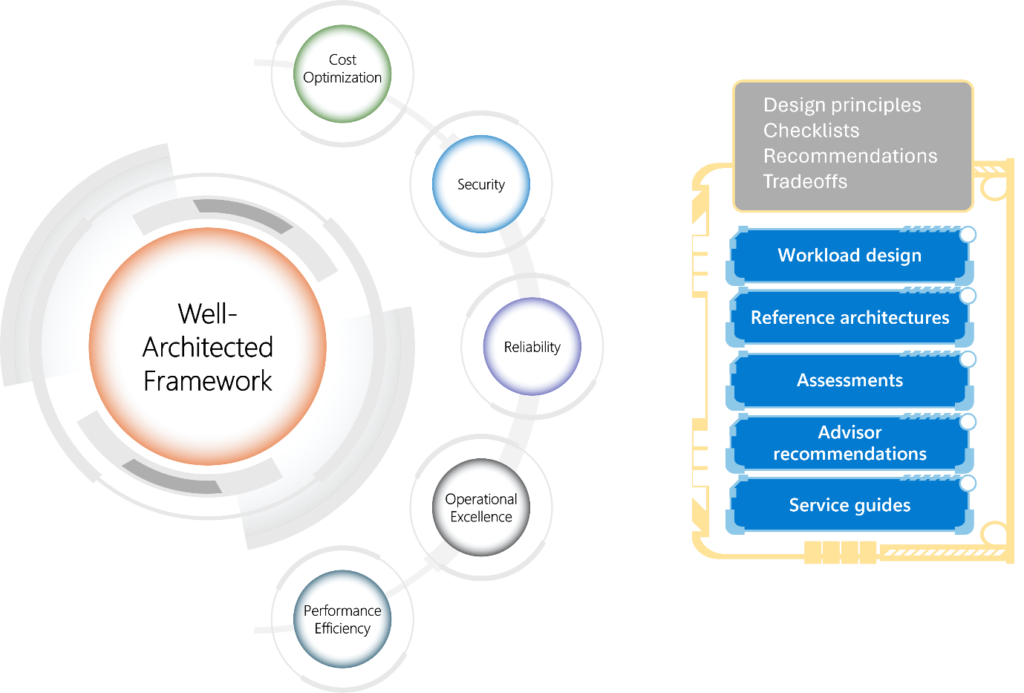
The Azure Well-Architected Framework (WAF) encompasses five essential tenets that guide solution architects in building robust and efficient workloads on Microsoft Azure:
- Reliability:
- Ensures that your workload meets uptime and recovery targets by incorporating redundancy and resiliency at scale.
- Key considerations include high availability, fault tolerance, and disaster recovery strategies.
- Security:
- Safeguards your workload from attacks by maintaining confidentiality and data integrity.
- Focus areas include identity and access management (IAM), encryption, and network security.
- Cost Optimization:
- Encourages an optimization mindset at organizational, architectural, and tactical levels.
- Strategies involve right-sizing resources, leveraging reserved instances, and optimizing spending within budget.
- Operational Excellence:
- Aims to reduce issues in production by building holistic observability and automated systems.
- Consider monitoring, logging, and automation practices.
- Performance Efficiency:
- Allows your workload to adapt to changing demands through horizontal scaling and testing changes before deployment.
- Optimize resource usage and performance.
These tenets collectively provide a strong foundation for designing and operating workloads on Azure, ensuring they deliver business value over time. Whether you’re hosting Oracle databases, optimizing SAP workloads, or building mission-critical applications, adhering to these principles contributes to a successful cloud journey!
Source: Azure Well-Architected Framework – Microsoft Azure Well-Architected Framework | Microsoft Learn
Let’s explore how you can implement the five tenets of the Azure Well-Architected Framework (WAF) in your architecture:
- Reliability:
- High Availability: Design your workload to run across multiple Azure Availability Zones for redundancy. Use Azure Load Balancer to distribute traffic.
- Fault Tolerance: Implement Azure Application Gateway with multiple instances to handle failures gracefully.
- Disaster Recovery: Set up Azure Site Recovery for seamless failover to a secondary region.
- Security:
- Identity and Access Management (IAM): Use Azure Active Directory (AD) for user authentication and authorization.
- Encryption: Encrypt data at rest using Azure Disk Encryption or Azure Storage Service Encryption.
- Network Security: Configure Azure Network Security Groups (NSGs) to control inbound and outbound traffic.
- Cost Optimization:
- Resource Sizing: Right-size your VMs and databases based on workload requirements.
- Reserved Instances: Leverage Azure Reserved VM Instances for predictable workloads.
- Monitoring and Cost Analysis: Use Azure Cost Management and Billing to track spending.
- Operational Excellence:
- Monitoring and Logging: Set up Azure Monitor for real-time insights into performance and issues.
- Automation: Use Azure Logic Apps or Azure Functions for automated tasks.
- Change Management: Implement Azure DevOps for continuous integration and deployment.
- Performance Efficiency:
- Horizontal Scaling: Use Azure Autoscale to dynamically adjust resources based on demand.
- Testing and Optimization: Load test your application using Azure Application Insights.
- Content Delivery: Utilize Azure Content Delivery Network (CDN) for efficient content distribution.
Example: E-Commerce Application
- Reliability:
- High Availability: Design your application to run across multiple Azure Availability Zones for redundancy. Use Azure Load Balancer to distribute traffic.
- Fault Tolerance: Implement Azure Application Gateway with multiple instances to handle failures gracefully.
- Disaster Recovery: Set up Azure Site Recovery for seamless failover to a secondary region.
- Security:
- Identity and Access Management (IAM): Use Azure Active Directory (AD) for user authentication and authorization.
- Encryption: Encrypt data at rest using Azure Disk Encryption or Azure Storage Service Encryption.
- Network Security: Configure Azure Network Security Groups (NSGs) to control inbound and outbound traffic.
- Cost Optimization:
- Resource Sizing: Right-size your VMs and databases based on workload requirements.
- Reserved Instances: Leverage Azure Reserved VM Instances for predictable workloads.
- Monitoring and Cost Analysis: Use Azure Cost Management and Billing to track spending.
- Operational Excellence:
- Monitoring and Logging: Set up Azure Monitor for real-time insights into performance and issues.
- Automation: Use Azure Logic Apps or Azure Functions for automated tasks.
- Change Management: Implement Azure DevOps for continuous integration and deployment.
- Performance Efficiency:
- Horizontal Scaling: Use Azure Autoscale to dynamically adjust resources based on demand.
- Testing and Optimization: Load test your application using Azure Application Insights.
- Content Delivery: Utilize Azure Content Delivery Network (CDN) for efficient content distribution.
Partner Tools with Azure Monitor Integration
Routing your monitoring data to an event hub with Azure Monitor enables you to easily integrate with external SIEM and monitoring tools. The following table lists examples of tools with Azure Monitor integration.
| Tool | Hosted in Azure | Description |
| IBM QRadar | No | The Microsoft Azure DSM and Microsoft Azure Event Hubs Protocol are available for download from the IBM support website. |
| Splunk | No | Splunk Add-on for Microsoft Cloud Services is an open-source project available in Splunkbase. If you can’t install an add-on in your Splunk instance and, for example, you’re using a proxy or running on Splunk Cloud, you can forward these events to the Splunk HTTP Event Collector by using Azure Function for Splunk. This tool is triggered by new messages in the event hub. |
| SumoLogic | No | Instructions for setting up SumoLogic to consume data from an event hub are available at Collect Logs for the Azure Audit App from Event Hubs. |
| ArcSight | No | The ArcSight Azure Event Hubs smart connector is available as part of the ArcSight smart connector collection. |
| Syslog server | No | If you want to stream Azure Monitor data directly to a Syslog server, you can use a solution based on an Azure function. |
| LogRhythm | No | Instructions to set up LogRhythm to collect logs from an event hub are available at this LogRhythm website. |
| Logz.io | Yes | For more information, see Get started with monitoring and logging by using Logz.io for Java apps running on Azure. |
ASIM and the Open Source Security Events Metadata (OSSEM)
OSSEM is a community-led project that focuses primarily on the documentation and standardization of security event logs from diverse data sources and operating systems. The project also provides a Common Information Model (CIM) that can be used for data engineers during data normalization procedures to allow security analysts to query and analyze data across diverse data sources.
ASIM aligns with the Open Source Security Events Metadata (OSSEM) common information model, allowing for predictable entities correlation across normalized tables.
ASIM components
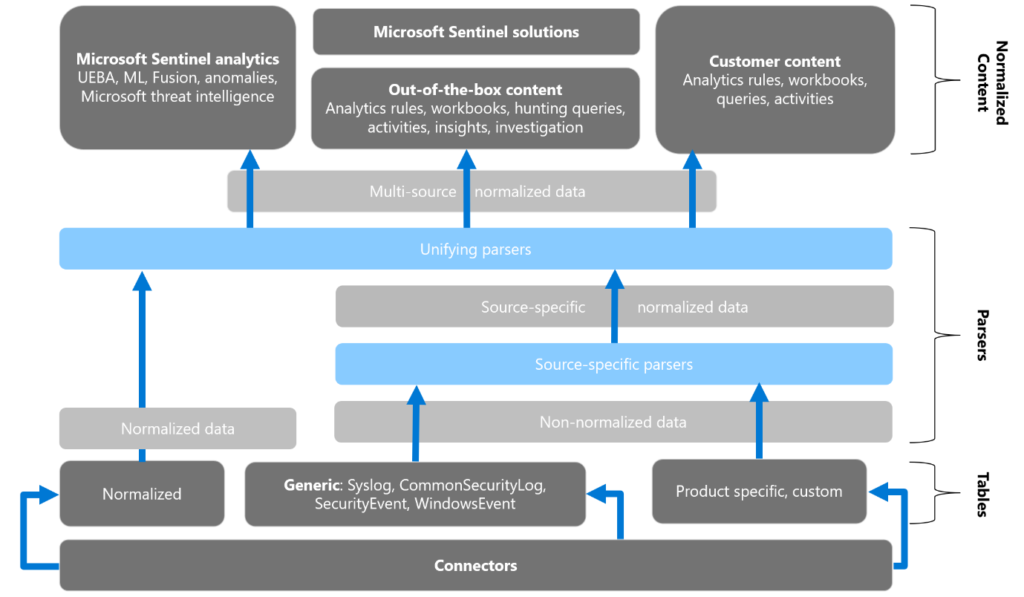
The following image shows how non-normalized data can be translated into normalized content and used in Microsoft Sentinel. For example, you can start with a custom, product-specific, non-normalized table, and use a parser and a normalization schema to convert that table to normalized data. Use your normalized data in both Microsoft and custom analytics, rules, workbooks, queries, and more.
Source: Normalization and the Advanced Security Information Model (ASIM) | Microsoft Learn
ASIM includes the following components:
Normalized schemas
Normalized schemas cover standard sets of predictable event types that you can use when building unified capabilities. Each schema defines the fields that represent an event, a normalized column naming convention, and a standard format for the field values.
ASIM currently defines the following schemas:
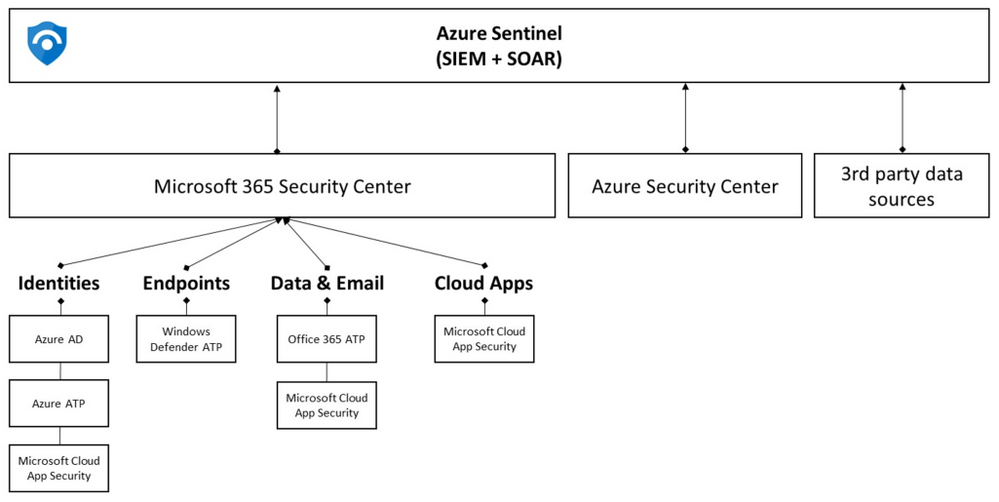
Azure Sentinel in other hand is a cloud-native Security Information and Event Management (SIEM) and Security Orchestration, Automation and Response (SOAR) tool. Azure Sentinel’s role is to ingest data from different data sources and perform data correlation across these data sources. On top of that, Azure Sentinel leverages intelligent security analytics and threat intelligence to help with alert detection, threat visibility, proactive hunting, and threat response. The diagram below shows how Azure Sentinel is positioned across different data sources:
Source: Integrating Azure Security Center with Azure Sentinel – Microsoft Community Hub
Integrating Security Center with Azure Sentinel
When you configure this integration, the Security Alerts generated by Security Center will be streamed to Azure Sentinel. You only need to follow a few steps to configure this integration, and you can follow those steps by reading this article. Once the integration is configured, the alerts generated by Security Center will start appearing in Azure Sentinel.
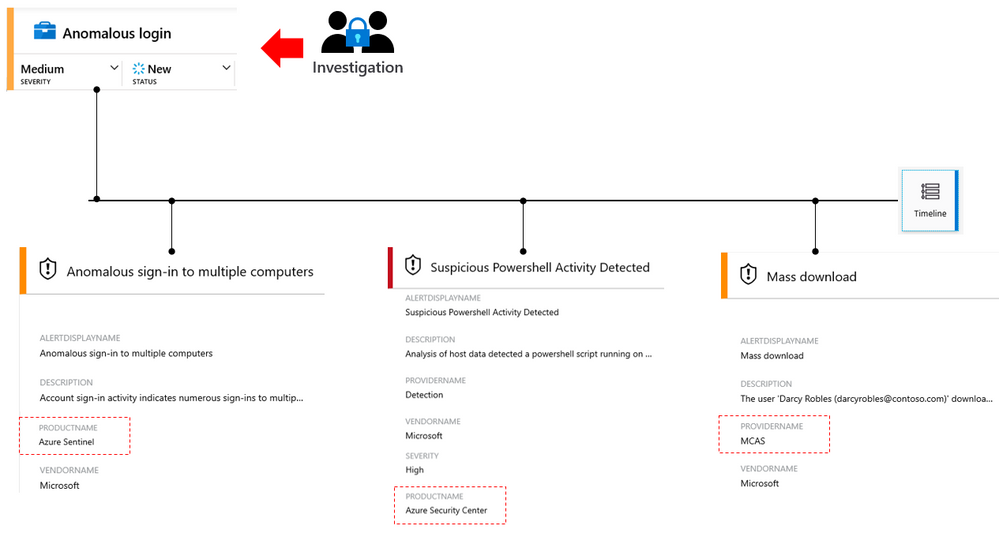
End-to-end visibility
One advantage of using Azure Sentinel as your SIEM is the capability to have data correlation across data sources, which enables you to have an end-to-end visibility of the security related events, as shown in the diagram below:
Source: Integrating Azure Security Center with Azure Sentinel – Microsoft Community Hub
In this example, Azure Sentinel created a case based on data correlation that is coming from different Microsoft products.